to limit sessions
/sbin/sysctl -w net.netfilter.nf_conntrack_max=xxxx
xxxx = number
/sbin/sysctl -w net.netfilter.nf_conntrack_count
to check how many sessions
Use this command to see all of the sessions: cat /proc/net/nf_conntrack
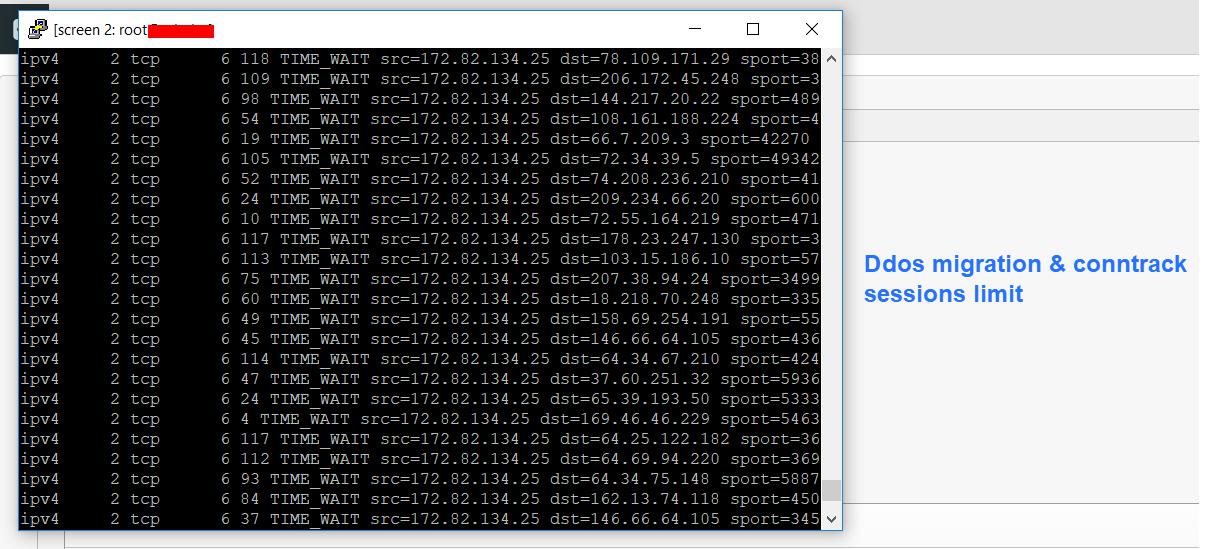
Now a day ddos attack is a big problem for a busy website. Today I am going to share some command about ddos migration and Limit conntrack sessions on cPanel server.
Login to SSH and execute following commands with root access:
1.To see what IPs are connecting to server and how many connections exist from each IP:
netstat -anp |grep 'tcp\|udp' | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
2.To see how many connections each IP on the server is receiving:
netstat -plan |grep :80 | awk '{print $4}' | cut -d: -f1 | sort | uniq -c | sort -n
3.Get total current active connections to Apache:
netstat -apn | grep :80 | wc -l
Get Apache status update from command line to see which domain is receiving maximum hits (cPanel/WHM server):
lynx http://localhost/whm-server-status
Once you get IPs having most connection from 1st command, now you need to add these IP to deny list. In this post i will not talk about configServer Firewall or any other firewall. As according to my experience if you have high packets DDOS attacks firewall does not help any more. So we will go with .htaccess solution.
Just add following below code in your .htaccess placed under main directory of web site, for cPanel account it is public_html/.htaccess if it does not exist just create it.
deny from (IP that is having too many connections)<pre> e.g: In below example 127.0.0.1 is assumed as IP having many connections, please replace it accordingly. <pre>deny from 127.0.0.1
Add same above code for each IP per line.
Use this command to see all of the sessions: cat /proc/net/nf_conntrack
Create, collaborate, and turn your ideas into incredible products with the definitive platform for digital design.
12 December 2022
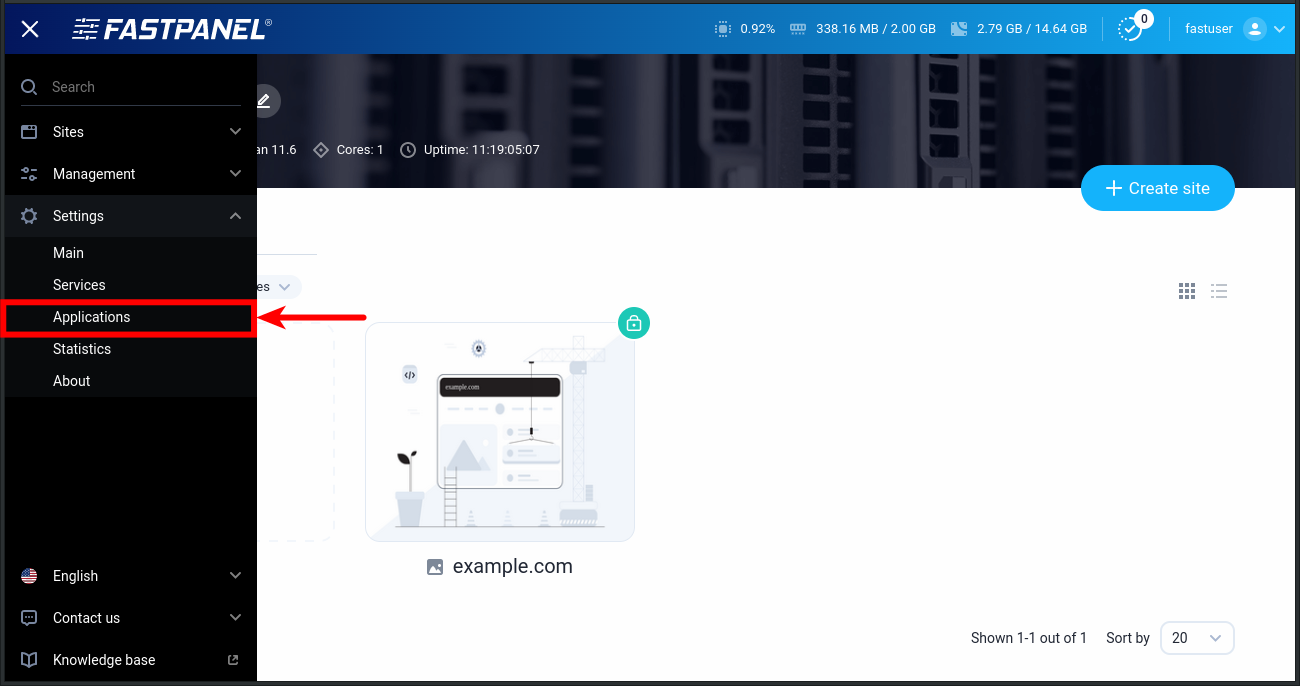
This article explains how you can create cPanel backup from the command line, using your own username and password.
12 December 2022
Webuzo is a popular alternative to cPanel, a widely used web hosting control panel developed by cPanel, Inc.
02 February 2022
NFT domains are new web extensions that are deployed using ERC 721 and Polygon Network, except .zil which uses Zilliqa.

01 January 2022
This document describes how to manually delete a MySQL® database from a cPanel & WHM server. This is useful if, for exa

11 November 2021
To transfer your domain with us then must need EPP Code.
Contact us at